Digital Banks Targeted In Account Takeover Scams
By Elad Schulman, Segasec

Financial services companies always have been primary targets for scammers, with account takeover the ultimate prize. If successful, phishing scams reward attackers with sensitive data they can use for financial gain, identity theft, or brand damage.
With this in mind, Segasec monitored several prominent digital banks between October 17th and November 5th. The research uncovered hundreds of dangerous URLs and many live attacks. Following is data on three targeted brands.
As background, Segasec was looking for suspicious URLs, “suspect” assets that might signal imminent attacks, and of course attacks in progress. Segasec acted without insider knowledge — none of the monitored companies were Segasec customers.
Live Attacks On Monzo.com And Chime
Monzo.com adds tens of thousands of new customers every week, making it one of the fastest-growing digital banks online today. During the monitoring period, Segasec identified 229 suspicious URLs and two possible attacks, including the screenshot below, which is a live website that uses the Monzo name and logo, and mirrors wording from the official Monzo site.

This site also uses the padlock symbol, which often times is enough to trick visitors into thinking a site is safe, when in fact it only confirms that the communication, not the content, is secure.
Meanwhile, research on Chime Bank turned up fewer suspicious URLs, but of the 71 discovered there were two possible attacks live at the time of monitoring.
Segasec reviewed URLs, domain registrations and certificates pertaining to Chime. In the below case, while the original Chime website domain was registered with GoDaddy in 2015, this new URL was registered with Name Cheap more recently, in 2019, which is a red flag.
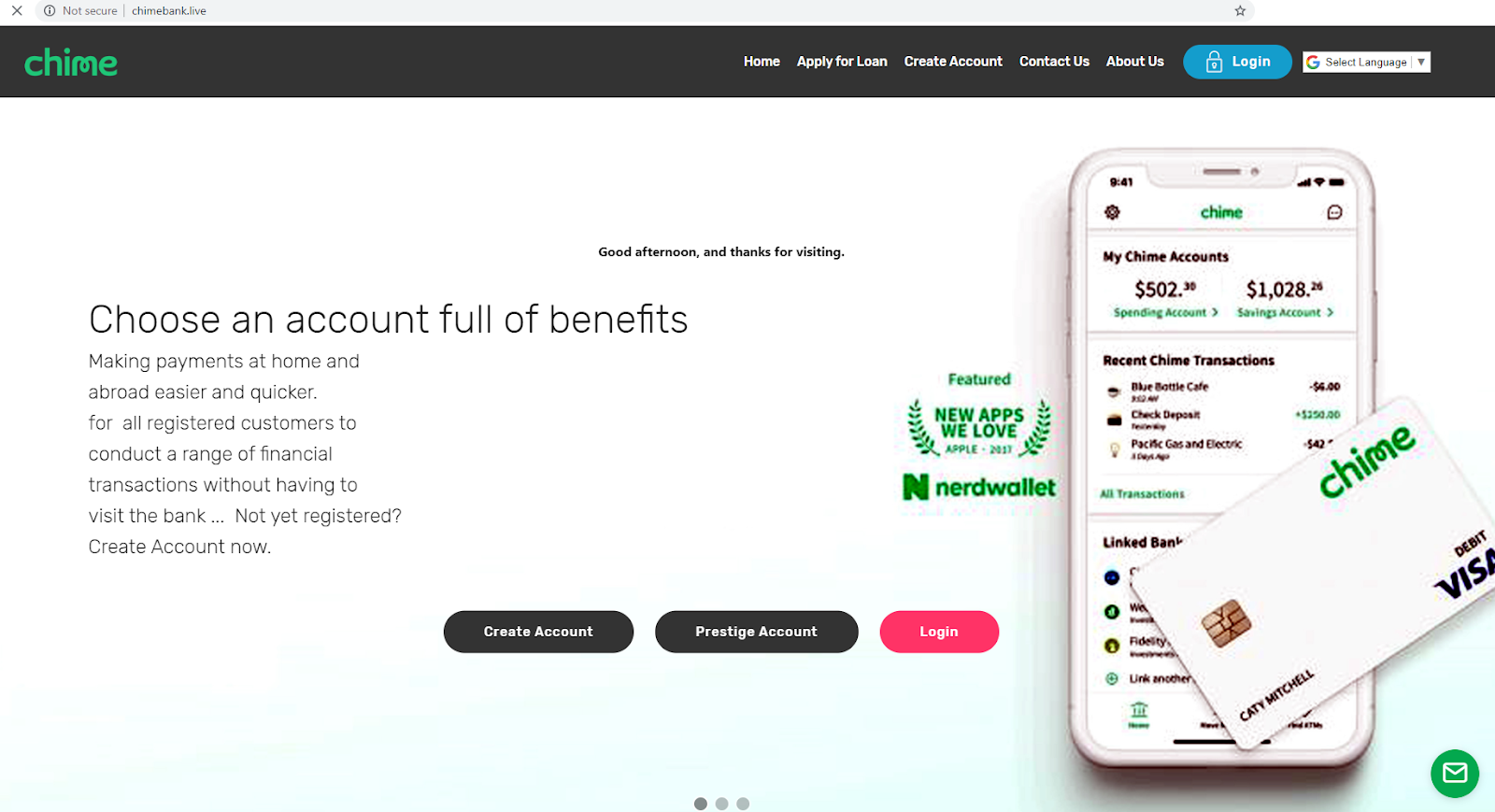
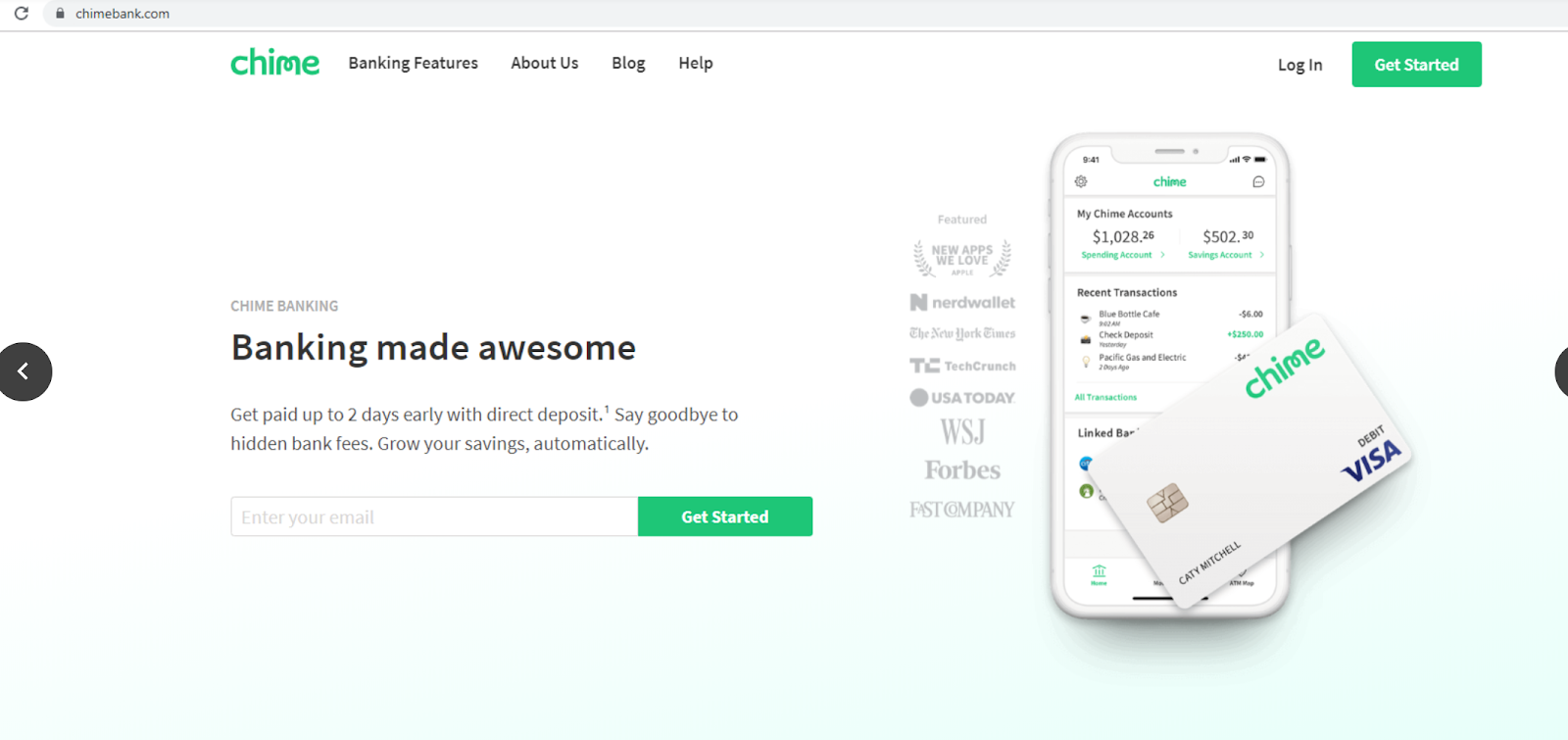
Compared to the real website (below), it's clear how far the hackers have gone to create a website that mimics the actual brand. Content scraping tools have been used to match the color scheme, images and fonts. It's not a stretch to imagine an unsuspecting customer logging in and handing over sensitive credentials.
Revolut Customers Attacked By ‘Invisible’ Punycode Scam
Revolut was, by far, the most targeted digital bank Segasec researched, with 367 suspicious URLs uncovered, 10 of which were possible attacks, including some that leveraged sophisticated tactics such as Punycode to fly beneath the radar.
Punycode uses words that cannot be written in the standard format for website links, such as Greek or Arabic characters, and converts them to Unicode so they appear legitimate. Behind the scenes, they are actually redirecting users to a fake website. In the example below, Segasec found that the IDN characters hxxp://xn--evolu-ip1bqf[.]com/ hosted a false website that appeared to users as http://revolut.com/.
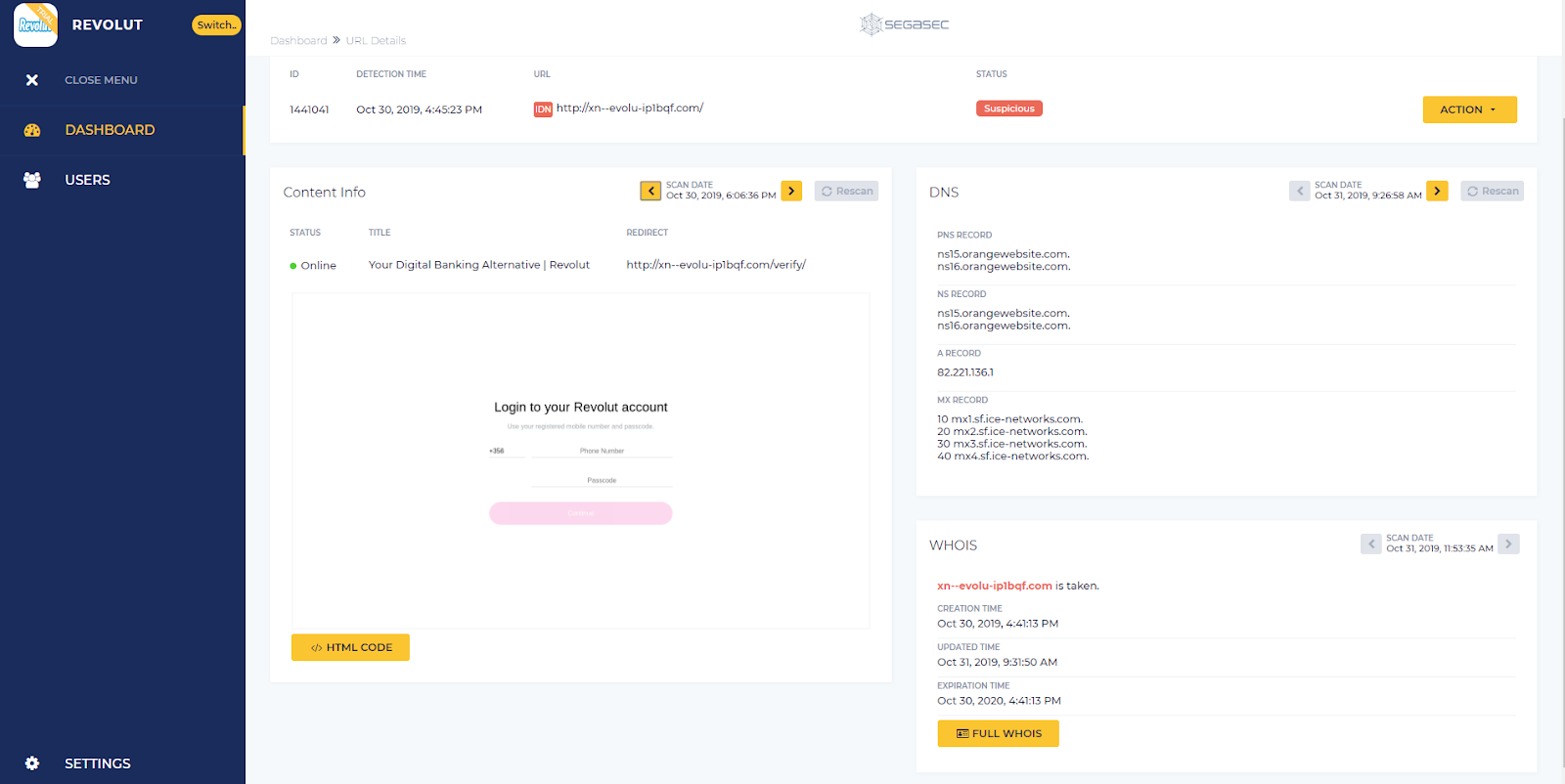
This data is just the tip of the iceberg, found during a limited monitoring period. Financial services is one of the most high-risk industries for cyber attacks, and companies have a responsibility to protect customer data. Segasec’s monitoring suggests the impact of cybercrime against financial institutions is growing. Following are a few tips to help financial services companies protect customers:
- Check your browser: In some cases, users can force-reveal Punycode URLs by changing search settings. This is a simple fix, but only works for browsers that offer the setting, such as Mozilla Firefox.
- Take a closer look at the URL: If any of the letters in the address bar look in any way strange, stop. Revisit the website using the correct URL, inputting it one letter at a time in a new window.
- Use up-to-date software: Make sure that you have updated antivirus software and browser plugins, which in some cases can catch this type of attack before customers fall victim.
About The Author
Elad Schulman is CEO of Segasec.
